Token Ring/FDDI Networks
An illustration of a token ring's token passing
General
A token passing ring LAN is a group of computers connected in a loop.
The group uses a token passing access mechanism. A computer wishing
to send data should first receive permission. When it gets control
of the network it may transmit a frame. Each frame transmitted on
the ring is transmitted from one computer to the next, untill it ultimately
returns to the initiator of the transmition.
The Token Passing Ring Network was originally developed by IBM and
only Ethernet LANs are more popular. The IEEE 802.5 specification which
was modeled after IBM's Token Ring is almost identical and the term Token
Ring is used to refer both specifications..
FDDI (Fiber Distributed Data Interconnect) is an improved token ring
specification based on fiber as the physical medum. As opposed to
Token Ring's single ring, FDDI, uses two to achieve better results.
CDDI, yet another standard, resembles FDDI, but uses a copper wire for
it's ring.
Characteristics
-
Comparison of basic characteristics
Technology
|
Data Rate (Mbps)
|
Maximum Segment Length (m)
|
Media
|
Rings
|
Recovery
|
| IBM Token Ring |
4/16
|
250 Shielded
72 Unshielded
|
Twisted pair |
1
|
Can handle a computer failure but canít recover from a broken connection. |
| IEEE 802.5 |
4/16
|
250
|
Not specified |
1
|
Can handle a computer failure but canít recover from a broken connection. |
| CDDI |
4/16
|
250 Shielded
72 Unshielded
|
Twisted pair |
2
|
Can recover from a brokenconnection (Self healing). |
| FDDI |
100
|
Unlimited
|
Optical fiber |
2
|
Can recover from a brokenconnection (Self healing). |
-
Topology
Token Ring LANs use a ring topology, i.e. each station is connected
to two other stations which are all together arranged in a loop.
Each station can send a signal along the loop after receiving permission
to do so (Only one station may have control on the network at
a specific point of time). The signal will travel from one station
to the other untill it reaches its initiator.
-
Priority System
Token Ring networks has a priority system that allows stations with
high priority to use the network more frequently. The priority is defined
by the frame's priority and reservation fields. In order to seize a token
a station must have priority which equals or is higher than the priority
field of the token. Only than the station can reserve the token for
the next pass around the network. This way when the next token is generated,
it includes the higher reserving station. Stations must change the priority
back to its previous value after theit transmision has completed.
-
Fault Management Mechanisms
In order to detect and correct network faults Token Ring networks may
dedicate a station for monitoring frames which are circuling around without
being dealt with. This monitor removes such frames and allow the network
to function in a normal manner all over again.
-
FDDI - Self healing
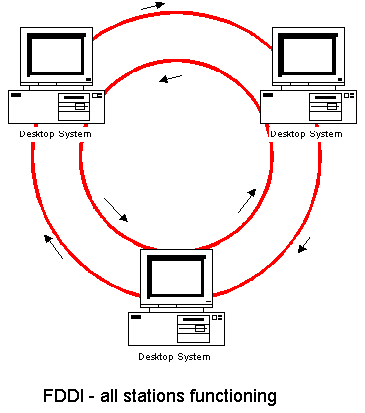
As described above FDDI networks implements a recovery mechanism which
enable the network to function properly even under a broken ring. FDDI
uses two rings to achieve recovery capabilities. As shown a token
is passed simultanioulsy on the network's inner and outer rings which backup
each other.
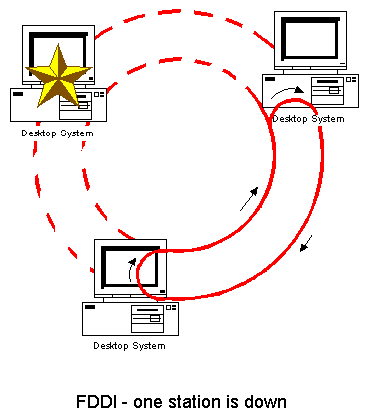
As shown in the following figure in case of broken connection
or station malfunction, the closest station closes the network loop
by sending the token it recieved from the outer/inner ring back using the
inner/outer ring. This feature is called Self healing.
Frame Format
Token Ring Frame Formats (tokens and data/command)
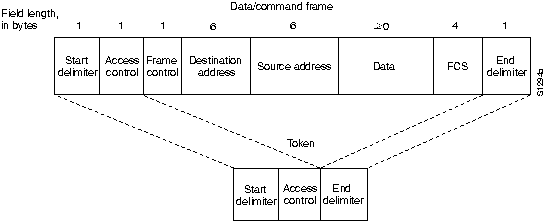
Tokens consist of:
-
Start delimiter - which alerts the stations of a token arrival (or data/command
frame).
-
Access control byte - which contains the priority and reservation fields,
a token bit to differentiate token from data/command frame and a monitor
bit checking whether a frame is circling the ring endlessly.
-
End delimiter - which signals the end of a frame, end of a logical sequence
and damaged frames.
Data/Command Frames carry information for upper-layer protocols.
After the Access control byte a frame control byte arrives and indicates
whether it is a data or control information (and which) frame. Then arrives
two address fields (source & destination) each 6 bytes long. Data follows
these fields (its length depends on the time each station can hold a token)
and then a FCS (frame check sequence) field. At the end as in tokens, an
end delimiter completes the frame.
Related topics
See Also




